Stop data breaches automatically.
- Cloud-native
- Agentless
- Automated
A powerful platform trusted by
more than 7,000 organizations worldwide.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”

Michael Smith, CISO
PRINCIPAL CLOUD SECURITY ENGINEER
Dynamic Switchback with Image and Carousel
Dynamic Switchback with Image and Carousel
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith II, CISO
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith III, CISO

Dynamic Switchback with Video on left and List
Dynamic Switchback with Video on left and List
Varonis shows you where sensitive data is concentrated and automatically remediates overexposure—getting you to least privilege without human intervention. Our machine learning analyzes permissions and user behavior to highlight where users have access to data they don't use or need. Link example.
- Magna ipsum lorem dolor justo Magna ipsum lorem dolor justo
- Magna ipsum lorem dolor justo Magna ipsum lorem dolor justo
Other DSPM solutions drown you in findings.
Varonis automates outcomes.
Real-time visibility
Always know where your sensitive data is, who has access to it, and how it is being used.
- Hybrid data discovery and classification
- Continuous exposure analysis
- Real-time data monitoring
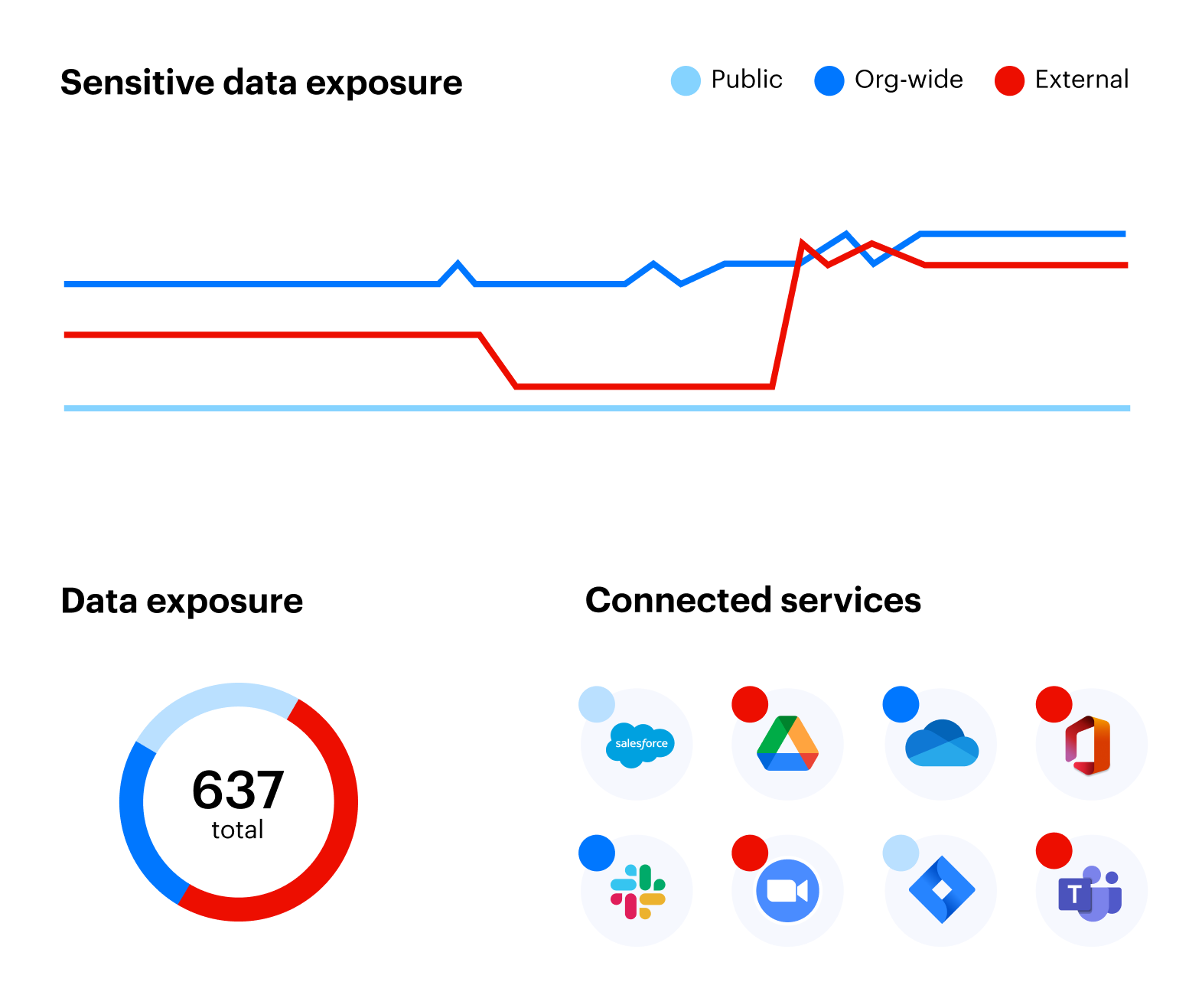
Automated prevention
Always know where your sensitive data is, who has access to it, and how it is being used.
- Hybrid data discovery and classification
- Continuous exposure analysis
- Real-time data monitoring
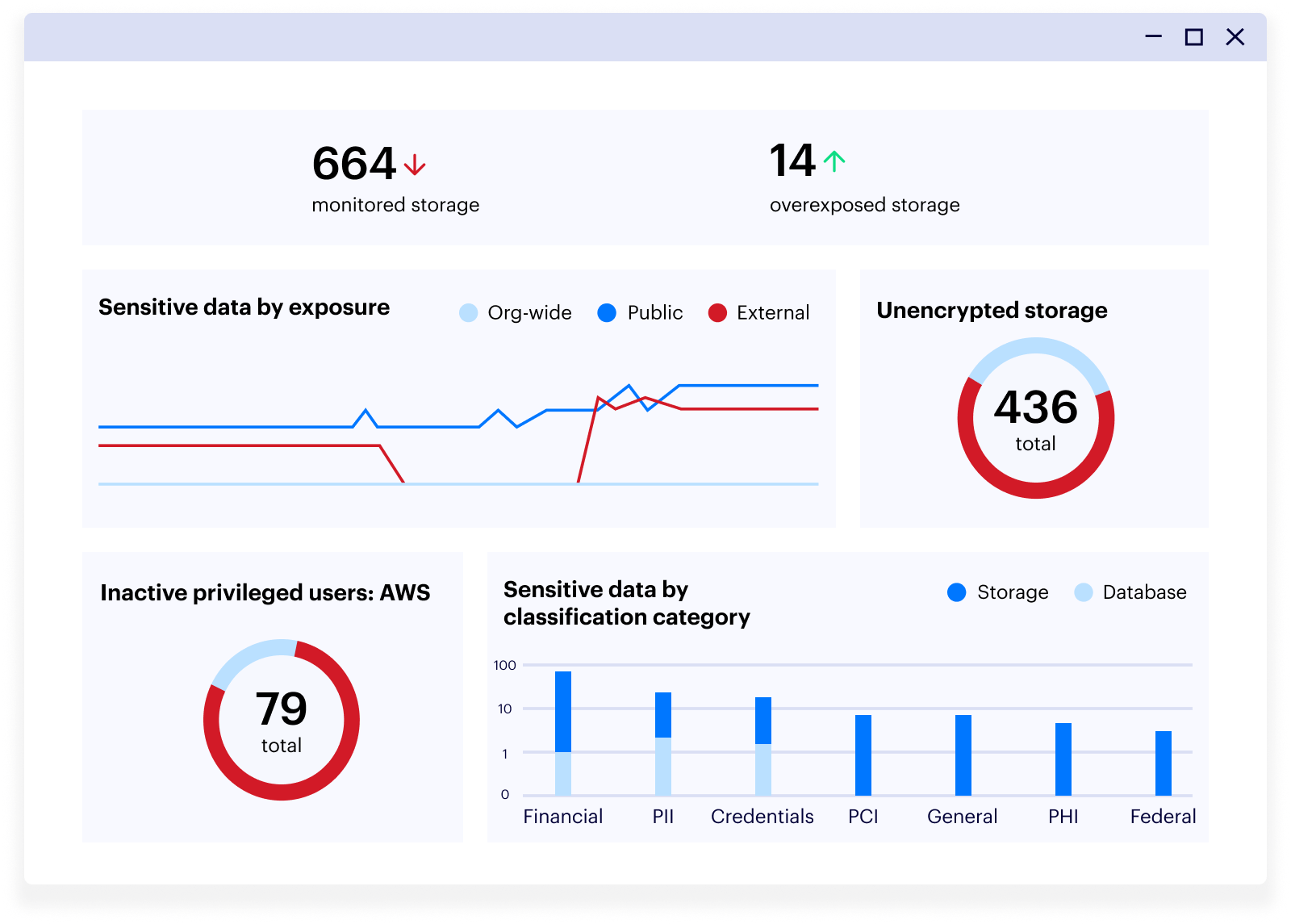
Proactive detection
Always know where your sensitive data is, who has access to it, and how it is being used.
- Hybrid data discovery and classification
- Continuous exposure analysis
- Real-time data monitoring



Webinar
State of Cybercrime: REvil and the New Windows Vulnerability
June 7, 3 p.m. ET / 8 p.m. BT
Dream Downtown & PHD Rooftop Lounge
355 W 16th St. New York, NY 10011
Description goes here. Observe cómo un atacante utiliza la cuenta personal de Gmail de un usuario para obtener acceso a un repositorio corporativo de GitHub.

Reserve your spot.
Reduce your blast radius.
Reduce your blast radius.
Reduce your blast radius.
Test heading
Connect Varonis to the security and privacy tools in your tech stack via ready-made apps and API-based integrations.
Thanks for your demo request!
Le mostraremos exactamente cómo se realiza este ataque, luego destacaremos cómo DatAdvantage Cloud facilita la visualización y la prevención de los ataques entre nubes.
Agenda

Presenters

Presenter Name

This is a bio section that will allow folks to write a much longer paragraph than the previous version.
Curabitur blandit tempus porttitor. Donec sed odio dui. Donec sed odio dui. Praesent commodo cursus magna, vel scelerisque nisl consectetur et. Maecenas faucibus mollis interdum. Aenean lacinia bibendum nulla sed consectetur. Cras justo odio, dapibus ac facilisis in, egestas eget quam. Aenean lacinia bibendum nulla sed consectetur. Integer posuere erat a ante venenatis dapibus posuere velit aliquet. Integer posuere erat a ante venenatis dapibus posuere velit aliquet.

Presenter Name

This is a bio section that will allow folks to write a much longer paragraph than the previous version.
Curabitur blandit tempus porttitor. Donec sed odio dui. Donec sed odio dui. Praesent commodo cursus magna, vel scelerisque nisl consectetur et. Maecenas faucibus mollis interdum. Aenean lacinia bibendum nulla sed consectetur. Cras justo odio, dapibus ac facilisis in, egestas eget quam. Aenean lacinia bibendum nulla sed consectetur. Integer posuere erat a ante venenatis dapibus posuere velit aliquet. Integer posuere erat a ante venenatis dapibus posuere velit aliquet.

Presenter Name

This is a bio section that will allow folks to write a much longer paragraph than the previous version.
Curabitur blandit tempus porttitor. Donec sed odio dui. Donec sed odio dui. Praesent commodo cursus magna, vel scelerisque nisl consectetur et. Maecenas faucibus mollis interdum. Aenean lacinia bibendum nulla sed consectetur. Cras justo odio, dapibus ac facilisis in, egestas eget quam. Aenean lacinia bibendum nulla sed consectetur. Integer posuere erat a ante venenatis dapibus posuere velit aliquet. Integer posuere erat a ante venenatis dapibus posuere velit aliquet.

Presenter Name

This is a bio section that will allow folks to write a much longer paragraph than the previous version.
Curabitur blandit tempus porttitor. Donec sed odio dui. Donec sed odio dui. Praesent commodo cursus magna, vel scelerisque nisl consectetur et. Maecenas faucibus mollis interdum. Aenean lacinia bibendum nulla sed consectetur. Cras justo odio, dapibus ac facilisis in, egestas eget quam. Aenean lacinia bibendum nulla sed consectetur. Integer posuere erat a ante venenatis dapibus posuere velit aliquet. Integer posuere erat a ante venenatis dapibus posuere velit aliquet.








Key features
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
Awesome feature that you want
Consectetur adipiscing elit. Quisque vestibulum maximus suscipit. In tellus risus, iaculis laoreet libero fsadlfjsla
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“Background map and background color can be changed in content editor.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”

Kelly Williams
Senior Data Security Analyst, Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
“I deal with many vendors all year. Varonis has far and away the best support. Super quick response time, expert advice, and all the guidance and help you could ask for.”
Amerisure Companies
The #1 Data Security Platform on the planet.




Get started with our world-famous data risk assessment.
- Critical findings report
- 1x1 with a data security expert
- Access to the entire Varonis Security Platform
- Another bullet!

Get started with our world-famous data risk assessment.
- Critical findings report
- 1x1 with a data security expert
- Access to the entire Varonis Security Platform
- Free incident response team




