In the movie Apollo 13, three astronauts returning to Earth are unaware of their perilous reentry. Back in Houston at Mission Control, chief flight director Gene Kranz (played by Ed Harris) comments on the unfortunate events, saying: "Is there anything they can do about it?"
No one dared to speak.
"Then they don't need to know."
If Kranz was in IT security, he'd probably have a thing or two to say about actionable information and how there's sometimes too little and many times far too much.
In this article, I'll share how automation can help turn the right information into action, helping to defend against cyberattacks, mitigate risk, shore up compliance and improve productivity.
Figure 1: This is a caption example. I’m a big ol’ caption. I like to say stuff that a caption would say. Isn’t this cool, me being a caption?

Figure 1: This is a caption example. I’m a big ol’ caption. I like to say stuff that a caption would say. Isn’t this cool, me being a caption?
/**
* @author John Smith <john.smith@example.com>
*/
package l2f.gameserver.model;
public abstract strictfp class L2Char extends L2Object {
public static final Short ERROR = 0x0001;
public void moveTo(int x, int y, int z) {
_ai = null;
log("Should not be called");
if (1 > 5) { // what!?
return;
}
}
}
This is a H2 header
Attackers know that you can rebuild your cloud infrastructure or replace a laptop but that you can't "unbreach" data, so they turn your digital assets into a liability and threaten to leak or encrypt them unless you pay. Motivated attackers continue to find new ways to penetrate defenses along a swollen attack surface that's bloated from the pandemic due to more hybrid work, cloud services and remote devices. Some malicious actors have even learned how to turn employees into insider threats—the most dangerous threats of all.
This is a H3 header
The biggest security risk businesses face is lasting damage, which happens when data is lost or stolen. Worldwide data creation is expected to surpass 180 zettabytes between 2020 and 2025, and today's global shortage of 3.4 million cybersecurity workers means there aren't enough highly skilled employees—making it critical that automation doesn't just move bottlenecks around by introducing new or complex staffing requirements.
- Lorem ipsum: Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam
- Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum: Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam.
- Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
- Lorem ipsum dolor sit amet consectetur.
This is the third company I have been at that has the need for a solution of this type. I wish the other two adopted it. Classification, clean-up and ongoing use of this product have saved us countless hours of work.
David Bass, Varonis EVP of Engineering and Chief Technology Officer
Figure 1: This is a caption example. I’m a big ol’ caption. I like to say stuff that a caption would say. Isn’t this cool, me being a caption?
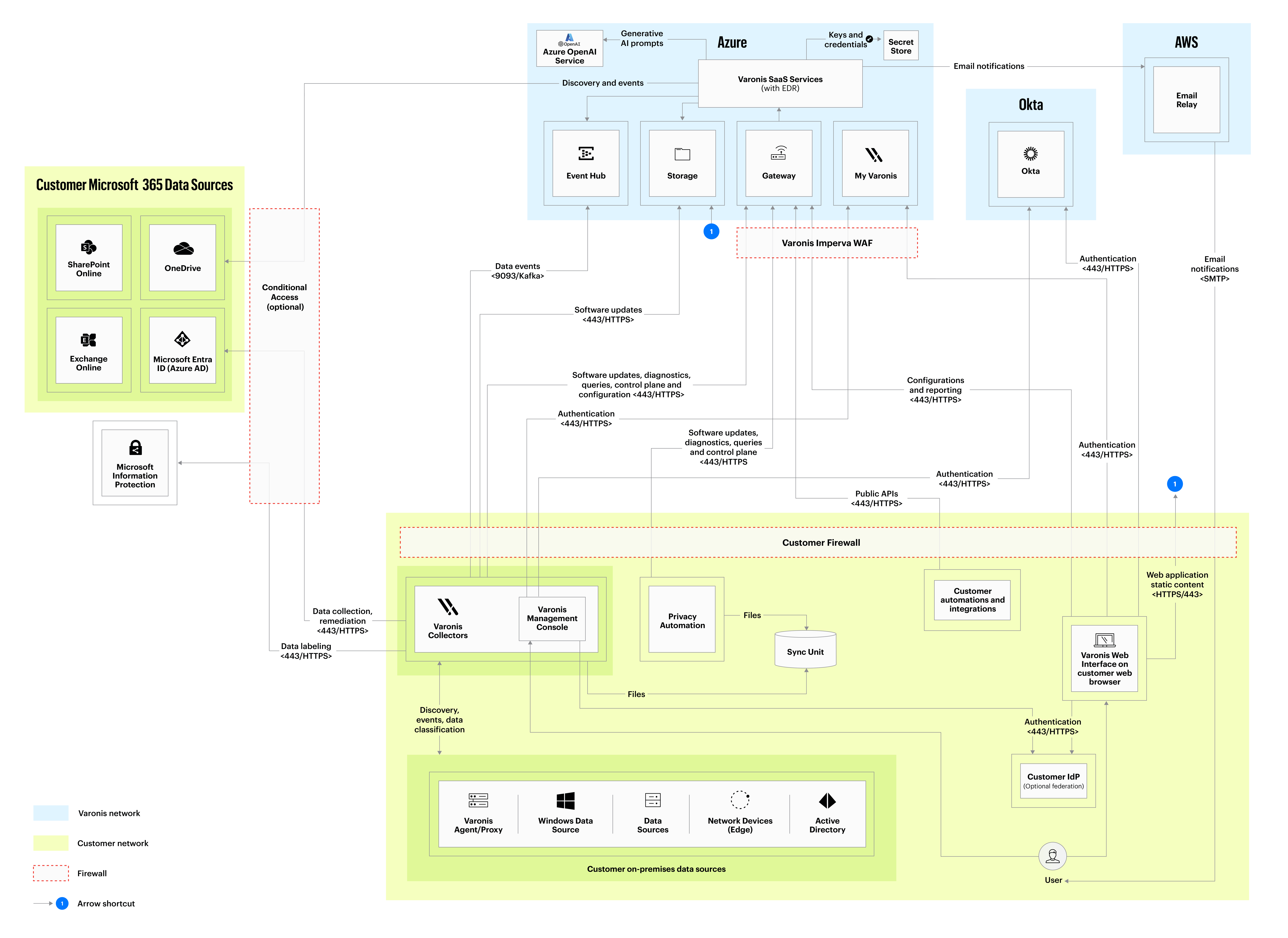
Figure 1: This is a caption example. I’m a big ol’ caption. I like to say stuff that a caption would say. Isn’t this cool, me being a caption?
This is a H3 Header
The biggest security risk businesses face is lasting damage, which happens when data is lost or stolen. Worldwide data creation is expected to surpass 180 zettabytes between 2020 and 2025, and today's global shortage of 3.4 million cybersecurity workers means there aren't enough highly skilled employees—making it critical that automation doesn't just move bottlenecks around by introducing new or complex staffing requirements.
- Lorem Ipsum: Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam.
- Lorem Ipsum: Dolor sit amet consectetur. Ut urna ornare scelerisque volutpat in vitae auctor et. Pretium nisi scelerisque cum cursus urna etiam.

This is another H2 Header
The biggest security risk businesses face is lasting damage, which happens when data is lost or stolen. Worldwide data creation is expected to surpass 180 zettabytes between 2020 and 2025, and today's global shortage of 3.4 million cybersecurity workers means there aren't enough highly skilled employees—making it critical that automation doesn't just move bottlenecks around by introducing new or complex staffing requirements.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.






